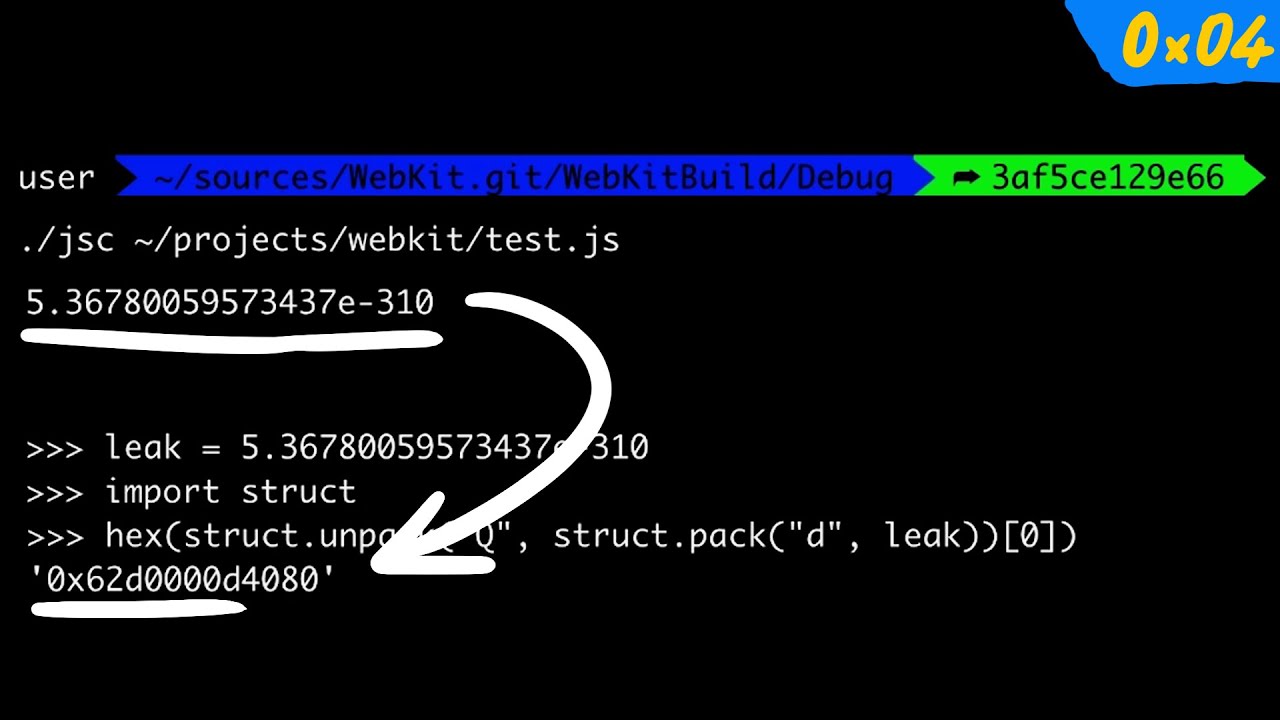
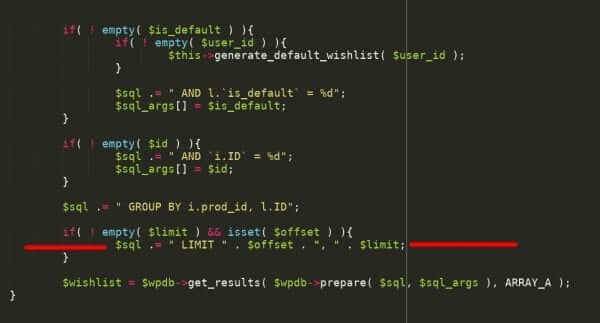
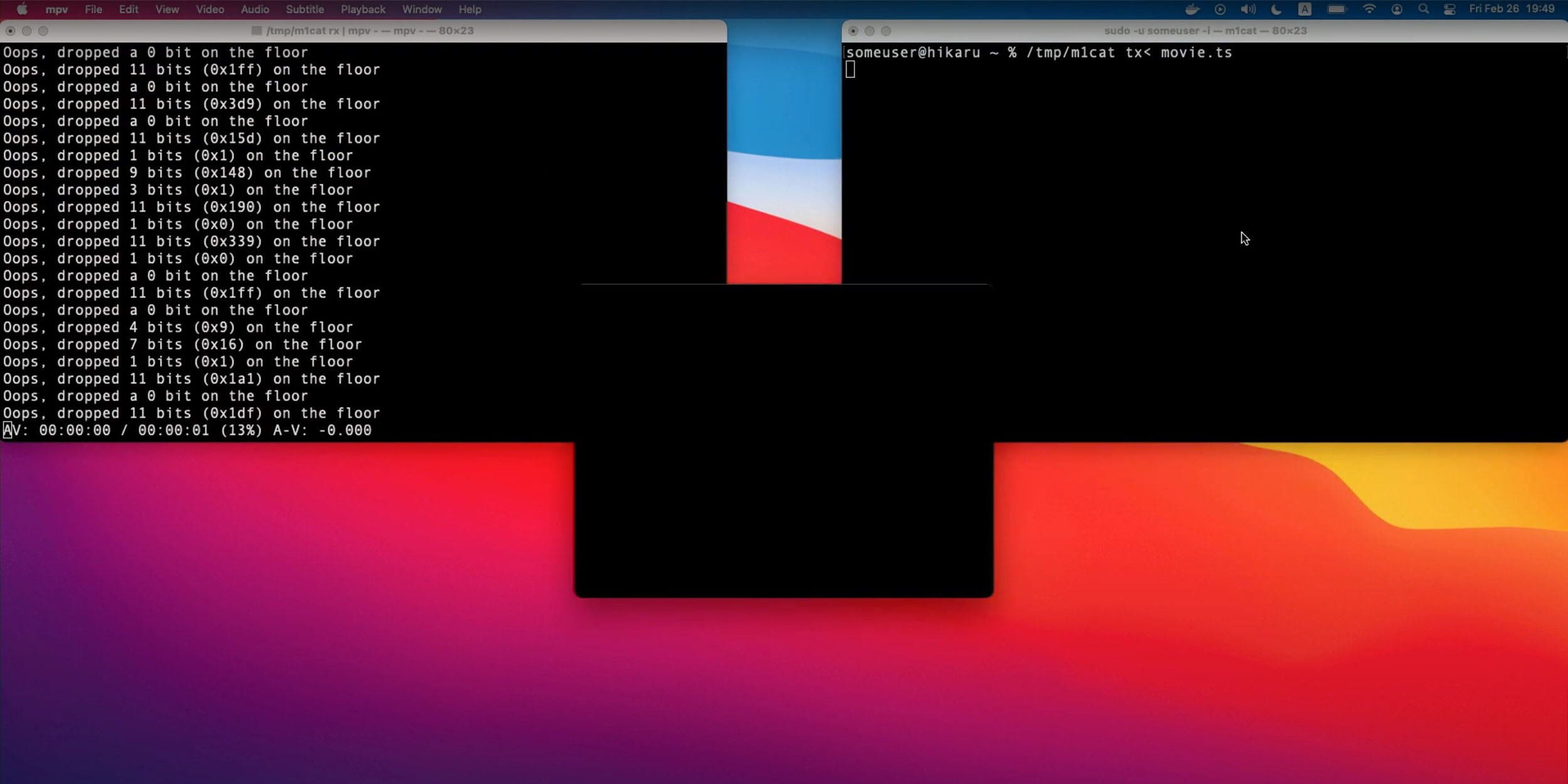
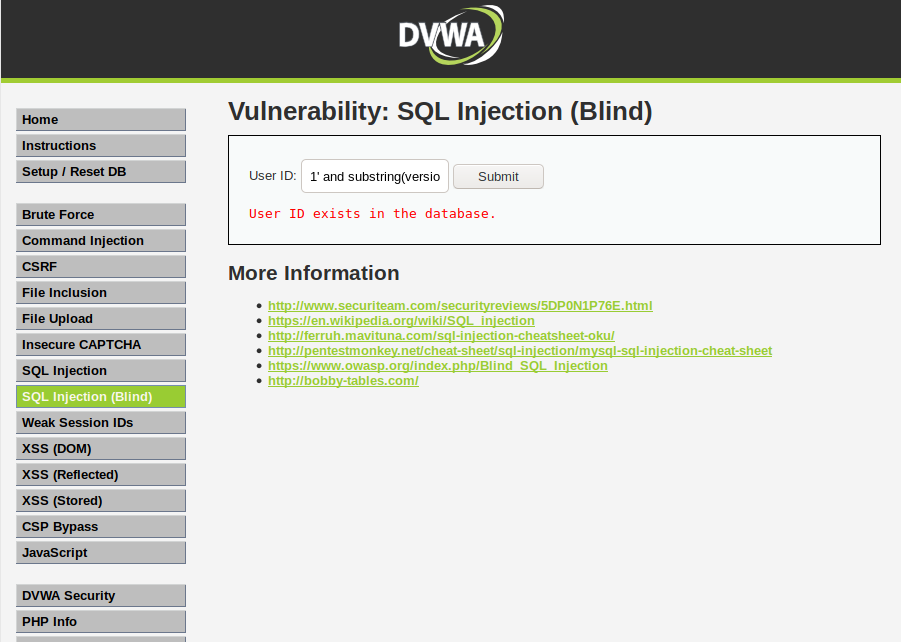
Patrick Walton on Twitter: "This just in: Rust is useless because everyone who can write Rust already writes safe C code. I guess I've just been imagining every browser vulnerability of the
Prototype pollution: The dangerous and underrated vulnerability impacting JavaScript applications | The Daily Swig

Remote code execution vulnerability exposed in popular JavaScript serialization package | The Daily Swig

markstats on Twitter: "Additional graph shows how often European clubs attempt long throw-ins and the outcome (xGD10) Brentford - positive, many long throw-ins Barcelona - positive, close to zero long throw-ins Bayern -